-
Amazon Rekognition: Comprehensive Guide to AWS Image and Video Analysis
If you’ve ever marveled at how modern applications can instantly recognize faces, objects, or even text within a single click,…
-

Amazon Rekognition: Comprehensive Guide to AWS Image and Video Analysis
-

User Account Management Best Practices for Secure Access
-

How to Automate User Verification with KYC API
-

Understanding Hash Encryption and How Cryptography Safeguards Data
-

IdP Identity Provider Explained: Key Features, Benefits & Trends
-

SMS Authentication: How It Works, Security Risks & Best Practices
-

Fraud Monitoring Strategies: Expert Guide to Proactive Threat Defense
-

Identity Lifecycle Management: A Comprehensive Guide for Modern Organizations
-

Unlocking Stronger Security: What Is a YubiKey?
-

The Power of Authentication Frameworks Explained
-

A Closer Look at PrivateID UltraPass for Photo ID Capture
-

Age Assurance in Digital Spaces and Why It Matters
-
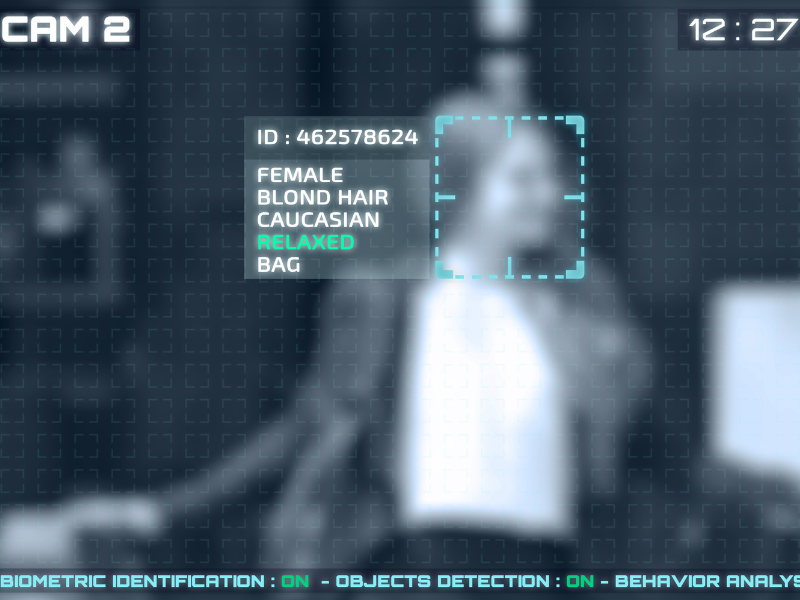
Deepfake Detection and the New Reality of Digital Proof
-

Biometric Authentication and Its Role in Modern Digital Security
-

Effective Identity Verification Strategies for Building Digital Trust